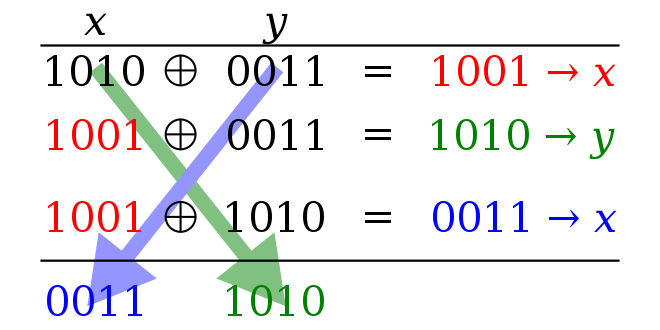
Review my works!
Two years have been passed since I started work in company and it is fourth-year in operating a tech blog!
Background
It has been about 4 years since I started this tech blog. To write and review about why I started blog and how this blog will go. And also I’d like to write about my future will.
Nowdays when I’m writing blog I think in my head “Do I need to be specific like this?”, “I think there needs more information…”, “Should I need to care about design and text layout like this?” and “Is this post too easy?” or “Too narrow field?”. It has come to take into account the number of real-time users and the number of daily users. Since then, I started thinking about where to focus. Is my blog the place of summarzing what I learned? or I studied? or all of them?
I am going to write just following of my thingkings. So it can be a bit messy. HaHa!
Current Blog Status
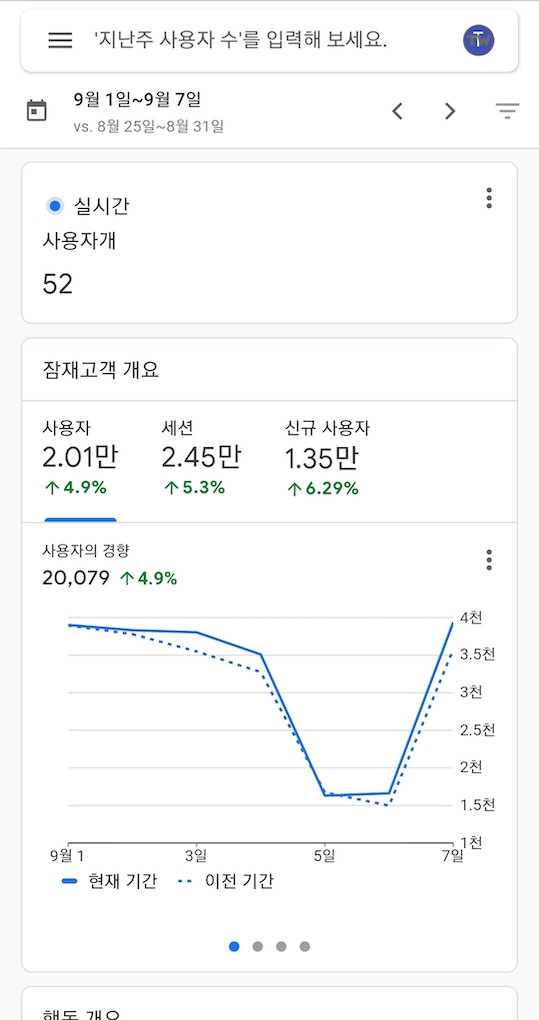
- In September, three months ago, about twenty thousand users per one week(it is dropped to ten thousand after COVID-19)
- In September, three months ago, about 50 realtime users(like above is is dropped to about 30 after COVID-19)
Since quite many people visit my blog so I can’t help but consider about quality. I got a dislike? similar button before because I commented that there was no problem on my system build but it was problem on VS build. Now that there are more people coming in, I become a bit greedy. I’d like to improve quality and hope visitors to get what they want when visiting my blog.
Recently number of visitors has been decreased after spread of COVID-19 and telecommuting.. I’m not sure it is just coincidence. Maybe it could be? Haha. I need more analysis for decreasing of visitors… Like this I have recently discovered that I consider visitors more than writing a blog. Care more about visitors then contents hmm.. Is that good?! Let’s write about that in next part.
When I Write Blog Until Now
- When I find something that I don’t know while studying or searching
- When I find something that I think it will be referenced in near future
- When I find something that is good for sharing to others
- When I get depressed or want to do something productive
Last two years, most blog posts are mainly written for what I learned in studying or for future using as reference. Mostly focuses on my curiosity and study. So sometimes the contents are very simple but some contents are long. Usually I have written post when I encoutner above first three cases while thinking about how to show and explain to others.
Lastly, I write post when I get depressed or want to do something productive. Because doing something productive can make me feel better. It is better than do nothing. This is tech blog so I’m not gonna write about my feelings!
Thinking When I Write Blog Nowdays
- Does it catch visitors eyes?
- Is it well organized and easy to understand?
- Can I remember when I read it in the future?
- Anything more needed?
Nowdays I think I too much concern about layout… This is place for writing what I learned but I’m getting more concern and care about number of visitors like writing a book. Of cource it is good to explain well and make pretty layout but I think nowdays I’m too much concern more about layout and shape than quality of the contents. It is the tail wagging the dog. I’d like to write professional quality content but now I’m focusing more on layout.
I think it is because visitors are keep growing. That is why I focus more on layout and design. From now I’d like to write blog in a different mindset.
Expected Shape Of My Future Blog
- Deep and professional content
- Contents of my daily studies and researches
Honestly there is no problem on my writing blog habits. Because I can fill my portfolio and visitors are keep visiting my blog. Even so, I’d like to improve myself more so I wrote above goals. After I found some of really deep and professional artificial intelligence and system blogs, it developed my desire of learning and depth.
I think my blog became the place where people can find what they want but what I want is more. That is, visitors who visit my blog improve themselves after visiting my blog. Yes improvement place! Also I’d like to deep dive into my professional field. I’m planning to write about latest technical things on Reddit or papers.
Specific Plan
- Add professional contents
- Keep the way of writing as usual
Keep writing as ususal and add more professional contents.
From now, I’d like to write about latest papers and technologies. It will take much more time than now… but I will try even though the writing interval gets longer.
“Write deep and professional quality content” is my future blog theme. Of course keep writing of what I learned and searched.
Other Things?
Blog template
Blog template has many features like search, tags, categories and showing all posts but because of many features it looks not pretty. However it is not a big concern so its priority is lower than other things.
Visitor data analysis
Visitors are decreasing.. I’m not sure it is because of COVID-19 I’d like to analyze my visitors data. First one is to analyze which contents are popular. I’m not sure it is worthy but just for curiosity
Visitor communication
I’d like to communitate with visitors using comment but Disqus is the only solution… I feel like to make my own comment service haha..
Many other things that left
I feel like I’ve been writing in a hurry to finish this because it is end of the year. There still many things are left… There are stories of customizing tags and other customized things. Also I’d like to add tools like FullStory service. I cannot list now but there are many funny and useful stories about my blog. It is a bit regrettable to not write about those things.
Wrap Up
Consistency is important. Let’s keep write! Even if the writing interval gets longer! At most!